Cryptocurrency-related hacking activity has reached a new and worrying level.
According to a report by Cisco Talos, the North Korean cybercriminal group known as 'Famous Chollima' appears to have stepped up its operations. Apparently, Famous Chollima is now focusing on job applicants in the crypto sector in India, using an entirely new method of attack.
Instead of carrying out blatant, large-scale attacks against crypto companies, as the Lazarus Group does, Famous Chollima has devised an ingenious strategy to gain access to companies in the sector.
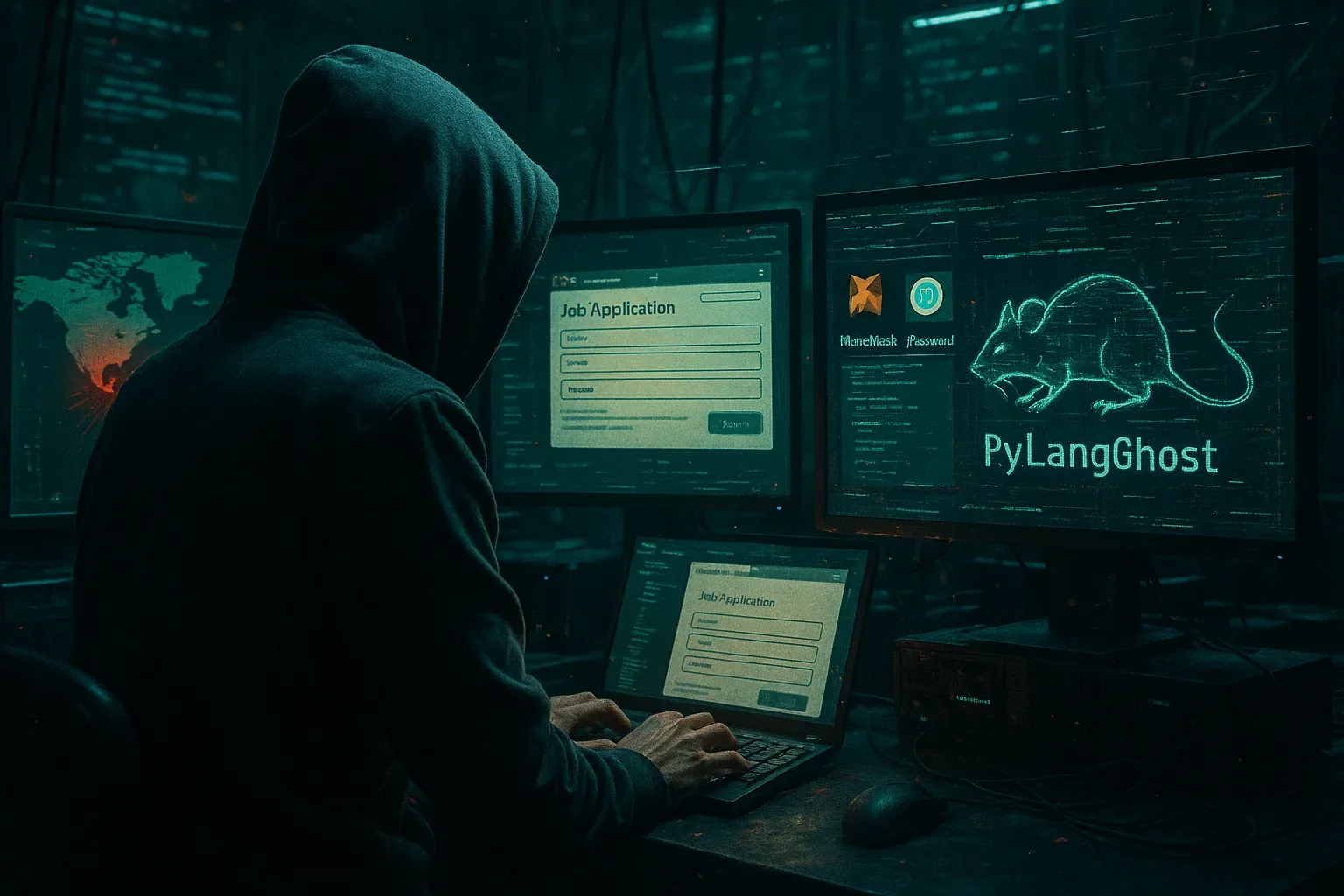
"Famous Chollima, a threat actor aligned with North Korea, is targeting blockchain and cryptocurrency professionals (mainly in India) with the new PylangGhost RAT, a Python version of their previous GolangGhost RAT," said Cisco Talos.
Famous Chollima, a North Korean-aligned threat actor, is targeting cryptocurrency/blockchain professionals (primarily in India) with the new PylangGhost RAT, a Python-based equivalent to their GolangGhost RAT: https://t.co/fYKvY1tXdB pic.twitter.com/ojDl6Oz7Zv
- Cisco Talos Intelligence Group (@TalosSecurity) June 18, 2025
According to Cisco Talos, "Famous Chollima" was first reported in mid-2024 or even earlier.
While the Lazarus Group is known to directly target - and in some cases extort - US-based crypto companies, such as Kraken, Famous Chollima takes a different approach: penetrating corporate networks via application forms.
Unlike the North Korean actions against Kraken and other companies, Famous Chollima's attacks do not use the applicants themselves to gain access to corporate systems.
Instead, they lure victims via fake recruitment sites that mimic famous crypto companies. However, the job applications are unbranded and include a seemingly nonsensical question: "What makes this technology application server so difficult?"
In addition to being poorly executed, these attacks run counter to the reputation of the Lazarus Group, known for its effectiveness. Cisco Talos points out that Famous Chollima is relatively amateurish.
The criminals lure victims through fictitious recruitment sites posing as technology or crypto companies. After submitting an application, the unsuspecting victim is invited to an online interview. During the supposed interview, the fake site asks the interviewee to type commands via the command line interface (CLI). They say the commands are to install video drivers, but in reality they download and run malicious software.
Once installed, the PylangGhost malware allows Famous Chollima to gain full access to the victim's computer. It is able to steal login information, browser history, and crypto wallet data.
In addition, the malware targets over 80 popular extensions, including MetaMask, Phantom, and 1Password.
The true target of the attack is still unclear. It is not known whether these actions are just isolated crimes or a first step towards a coordinated large-scale attack. It is possible that Famous Chollima is infecting the computers of these candidates in order to then impersonate them and more effectively infiltrate the crypto job market.
After the BITMEX case, in which it emerged that the Lazarus Group uses at least two separate teams - one low-level to infiltrate and one highly specialised to steal data - it is natural to wonder whether Famous Chollima also represents a hierarchical evolution of the North Korean hacker community.
Candidates for positions in the crypto world, especially in India, should be extremely careful. Be wary of unsolicited job opportunities. Never run commands on your system if you don't know the source.
It is also essential to secure end devices, use multi-factor authentication (MFA) and carefully monitor browser extensions.
Finally, it is important to verify the authenticity of recruitment portals before providing any personal or professional information.