A new, insidious wallet-emptying scheme has made its appearance in the crypto underground environment, increasing the pressure on an ecosystem already grappling with an unstoppable wave of phishing attacks.
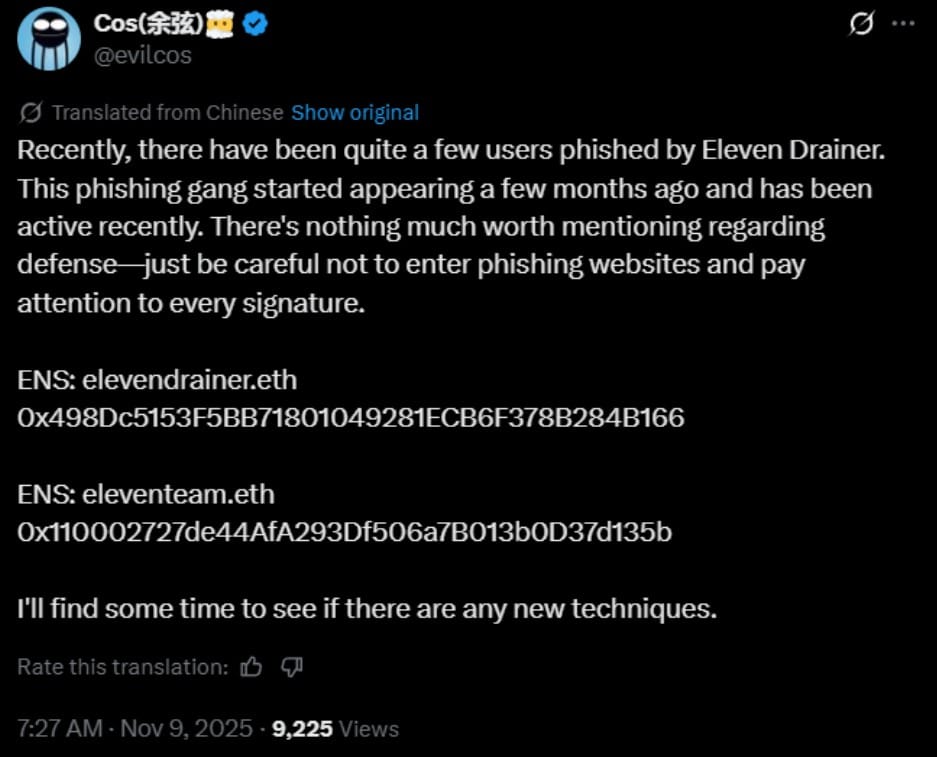
On 9 November, SlowMist founder Yu Xian announced that his team had identified a growing number of victims linked to a group known as Eleven Drainer. According to Xian, it is a new 'phishing-as-a-service' operator that has become increasingly active in recent weeks.
His observations indicate that the operators are expanding their reach and refining their techniques, prompting SlowMist researchers to examine whether the group has introduced more advanced exploitation methods.
The Black Market of "Phishing-as-a-Service" Expanding
Eleven Drainer joins a crowded landscape of professional "draining" service providers, such as Angel and Inferno Drainer. In recent years, this industry has flourished because it allows fraudsters to conduct large-scale malicious operations with minimal effort.
These phishing 'kits' provide everything an attacker needs, including website replicas, deceptive social media accounts, smart contract scripts, and automated workflows.
In return, the operators pocket a percentage of the stolen funds. As a result, these malicious actors have become the backbone of modern phishing crypto campaigns. In 2024, drainers were responsible for an estimated $494 million in losses, a 67 per cent jump from the previous year.
The User's Discipline: The Only True Defence
Despite the increasing sophistication of these groups, security specialists emphasise that user behaviour remains the weakest point in most incidents.
According to them, attackers leverage hasty decisions and misleading requests. In addition, they employ social engineering tactics to convince users to sign off on asset withdrawals without noticing the warning signs.
Xian emphasised this reality, noting that "there is not much to mention about defence" beyond disciplined online behaviour. His advice follows a clear logic: always avoid unfamiliar websites, scrutinise every wallet signature request, and refuse to approve transactions under pressure.








